GFI® Software has identified new variations of rogue security code aimed at businesses and consumers, often distributed through spam carrying the Blackhole exploit
London, UK, March 2012 : GFI Software has released its VIPRE® Report for February 2012, a collection of the 10 most prevalent threat detections encountered during the month. Most notably, GFI Labs has been documenting a new wave of fake antivirus applications (or rogue AV) on its Malware Protection Centre blog. Growing since the start of the year, last month brought a significant spike in new variations of rogue AV.
“While the velocity at which rogues were successfully propagating may have slowed toward the end of last year, they are certainly back now, and they remain a popular tactic among cybercriminals,” said Christopher Boyd, senior threat researcher at GFI Software. “Users should not let their guard down. As always – no matter how convincing they look – always take the time to evaluate any piece of software that claims your PC is infected, prompts you for a credit card number or asks you to share any sensitive data, especially if it’s software that you or your employer did not install.”
Many rogue AV programs are being distributed via spam containing malicious links to the Blackhole exploit, a tool used by cybercriminals to target unpatched vulnerabilities in software applications from industry leaders like Microsoft Corp. and Adobe Systems Inc. Users infected by rogue AV may be redirected to fraudulent websites, have their systems hijacked by software appearing to scan their PCs or plagued by messages warning of viruses and other PC security risk. These scareware tactics trick users into providing credit card data to purchase non-existent protection.
Rogue AV utilities are continually tweaked in an attempt to avoid detection, with newer variants of these malicious applications propagating every 12 to 24 hours. When confronted with suspected rogue AV, users can visit the Malware Protection Centre for removal advice or download GFI Software’s free virus removal tool, VIPRE® Rescue.
Movie Fans Targeted, Gamers Under Fire
Industry experts discovered that the personal web site of Twilight author Stephenie Meyer had been compromised, resulting in the site serving malware to visitors. The site had been compromised to host Crimepack, an exploit kit that takes advantage of known vulnerabilities of various Web browsers and the Windows® OS to install malware. Computers exploited by Crimepack can be turned into so-called ‘zombie’ clients, whereby criminal groups can control the infected machines remotely, using them to undertake an array of malicious tasks, such as spamming and launching denial of service (DoS) attacks.
Gamers were targeted via YouTube videos encouraging users to download a program that would generate codes that could be redeemed for free Microsoft Points, the online currency used by millions of Xbox® users worldwide. The bogus generator prompted the victim to fill out various surveys in order to receive a password and continue the code generation.
Despite the best efforts of Microsoft and a number of security specialists, the Kelihos Botnet has continued to gain momentum in the wild. Capable of sending out billions of spam emails in a day, Kelihos has been used to bombard users with spam relating to pornography, Viagra®, and fake pharmaceutical companies. After being suppressed towards the end of 2011, evidence uncovered by industry experts suggests that a new variant is on the loose, rebuilding the botnet and adding to the global spam burden.
Other high profile scams detected during February included a gift card scam that appeared on a fake Tumblr blog, in time for Valentine’s Day, which purported to be from lingerie firm Victoria’s Secret. With the company about to open its first UK outlets, we may see more localised examples of this in the coming months.
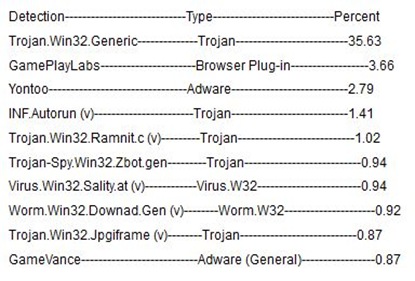
Top 10 Threat Detections for February
GFI’s top 10 threat detection list is compiled from collected scan data of tens of thousands of GFI VIPRE Antivirus customers who are part of GFI’s ThreatNet™ automated threat tracking system. ThreatNet statistics revealed that Trojans once again dominated the list, taking half of the top 10 spots.
About GFI Labs
GFI Labs specialises in the discovery and analysis of dangerous vulnerabilities and malware. The team of dedicated security specialists actively researches new malware outbreaks, creating new threat definitions on a constant basis for the VIPRE home and business antivirus products.
About GFI
GFI Software provides web and mail security, archiving and fax, networking and security software and hosted IT solutions for small to medium-sized businesses (SMB) via an extensive global partner community. GFI products are available either as on-premise solutions, in the cloud or as a hybrid of both delivery models. With award-winning technology, a competitive pricing strategy, and a strong focus on the unique requirements of SMBs, GFI satisfies the IT needs of organisations on a global scale. The company has offices in the United States, United Kingdom, Austria, Australia, Malta, Hong Kong, Philippines and Romania, which together support hundreds of thousands of installations worldwide. GFI is a channel-focused company with thousands of partners throughout the world and is also a Microsoft Gold ISV Partner.
This press release is presented for your information only.
Full Disclosure Statement: The GREEN (LIVING) REVIEW received no compensation for any component of this article.
This article is for your information only and the GREEN (LIVING) REVIEW does not (necessarily) approve, endorse or recommend the product, service or company mentioned.